VPN and fiber optic networks are not per se inherently secure. Hence, a company sharing its business between two or more office locations has to allocate extra resources to protect its IT network. For this security measure and the protection of sensitive company data, two complementary devices are required: Layer-2 encryptors and hardware security modules.
By Andreas Curiger
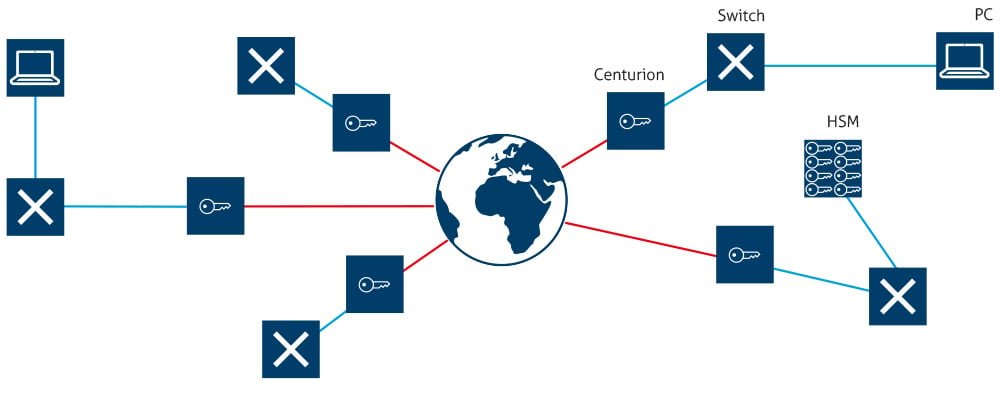
‘Private’ does not automatically indicate ‘protected’ or ’confidential’. The word ‘private’ just means the opposite of ‘public’. This also applies for a virtual private network VPN, which creates a kind of an intranet via a public network by integrating external sites into the company network. ‘Private’ in the context of a VPN hence means just that the private network will be logically separated from the public network. However, there is often no explicit protection against illicit access as encryption is not mandatory. The same sort of privateness applies to fiber optic networks: data might be illicitly tapped by organizations willing to invest some effort to get after it.
Hence, managing a company based in multiple locations implies protecting sensitive data in transit.
But how can that be accomplished? During transmission, data might be intercepted anywhere, and there are servers on which various processes might let things go wrong. As such, data will not adequately be protected. What’s more, data protection should not lead to a decrease of transmission speed nor data throughput.
The most effective measure against data theft is encryption.
Finally, security is also a matter of interaction of particular mechanisms and their respective implementation. The following principles will help to protect data effectively:


An effective choice of a security architecture implies the following considerations:
In order to be safe during transport and storage, sensitive data needs to be protected with two additional elements:
We recommend our Centurion encryptor and our Primus HSM for an optimal protection of your IT network.
The following publications of the scientific correspondent Christoph Jaggi provide a good insight into the world of layer-2 encryption. They have been receiving worldwide recognition.
Market overview:
English version: Layer 2 Encryptors for Metro and Carrier Ethernet, WANs and MANs; Market Overview Ethernet Encrypts for Carrier Ethernet, MPLS and IP Networks
Introduction:
English version: Layer 2 Encryptors for Metro and Carrier Ethernet; Ethernet Encryptors for Metro and Carrier Ethernet (an Introduction)
German version: Layer-2-Verschlüssler für Metro und Carrier Ethernet; Ethernet-Verschlüssler für Metro und Carrier Ethernet; die Einführung