If you have not heard about GDPR, here is a relevant link:
http://eur-lex.europa.eu/legal-content/EN/TXT/?uri=CELEX%3A32016R0679
The regulation requires to inform of the means of protection, particularly whether personal data is stored in encrypted form. Storing and transporting data in encrypted form and defined processes to access the data is a cornerstone in complying with GDPR. In many cases personal data is stored in databases, such as Oracle or Microsoft SQL server.  By encrypting these database your customers’ data is safe even when the database has been stolen provided that the corresponding encryption keys are securely stored. By storing the encryption keys in Hardware Security Modules (HSM) the highest level of key protection is achieved, since encryption keys cannot be taken out of the HSM.To protect your database there are several possibilities:
By encrypting these database your customers’ data is safe even when the database has been stolen provided that the corresponding encryption keys are securely stored. By storing the encryption keys in Hardware Security Modules (HSM) the highest level of key protection is achieved, since encryption keys cannot be taken out of the HSM.To protect your database there are several possibilities:
- Transparent Database Encryption (TDE): Encryption is built into the DB software using the TDE extension (only Oracle and MS-SQL) with the keys stored in an HSM
- Database Encryption Proxy/Wrapper: Fields that need privacy protection are encrypted on the fly with an encryption proxy/wrapper like Centraya JDBC/ODBC, which is inserted between application and database and storing of the keys in an HSM
- Pre-encrypting data records in the processing application
TRANSPARENT DATABASE ENCRYPTION (TDE)
Both Microsoft and Oracle provide TDE Modules to encrypt fields in their software packages. These packages come at an extra cost and can be immediately used for new databases. However, existing databases need to be converted to be used with TDE, turning on TDE on existing databases is not recommended. The reason for this is that often fields with names or social security numbers are used as indices. Once these fields are encrypted, links based on these indices will not work anymore.The steps to convert an database to use TDE are the following:- Add-on the license for TDE to your database software, set it up with key storage in the HSM.
- Create a new database that corresponds to your existing with a new indices field.
- Transfer all entries from the old database to new database with TDE enabled
- Test all applications with your new database
Access control and access monitoring should be implemented as to protect the data when in clear.
DB ENCRYPTION PROXY/WRAPPER
Database Encryption Proxy/Wrapper comes at a fraction of the cost of TDE licenses and can be inserted in between your applications and your databases. A proxy box with Database Encryption software like Centraya JDBC/ODBC encrypts fields (selectable) in your databases.
The following steps are required to encrypt a database with Encryption Proxy Software:
- Install and setup the DB Encryption Proxy inbetween your applications and your databases. Connect the Proxy to the HSM so that all keys are protected
- Select the fields that need encryption in the DB-EP
- Test your application
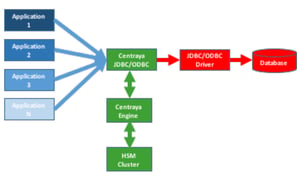
This setup only takes a few hours with the Centraya Inspection Mode by generating new profiles for the applications. The Centraya Engine also includes the necessary access control, monitoring, and rule engine. Multiple applications can use the same database.
All these measure require to store the encryption keys, safely, reliably, and highly accessible in a HSM for these measures to be effective.












