Integrated Technologies Directory
Discover how Securosys integrations provide comprehensive security, compliance, and reliability, empowering your organization to protect data and enhance operational efficiency across various platforms and services.
Welcome to the Securosys Integrations page, showcasing our extensive and ever-growing ecosystem of integrations with industry-leading platforms and services. Our integrations span cloud environments, cybersecurity solutions, privileged access management, and more. Leveraging Securosys Primus Hardware Security Modules (HSMs) on-prem or in the cloud, we provide unparalleled security, compliance, and reliability for a wide array of use cases.
Search a Integration
The Akeyless Gateway integration allows organizations to combine Akeyless’ Distributed Fragments Cryptography (DFC) with Securosys Primus HSM or CloudHSM for customer-controlled key fragments.
By storing the customer fragment securely inside a certified HSM, organizations retain direct control over a critical part of the encryption key while benefiting from Akeyless’ distributed secrets management architecture. This setup strengthens key ownership, reduces exposure risk, and supports highly secure, multi-cloud secrets protection.
Learn more.webp?length=680&name=AWS%20logo%20(1).webp) Securosys Proxy for AWS External Key Store (XKS)
Securosys Proxy for AWS External Key Store (XKS)
The Securosys Proxy for AWS External Key Store (XKS) allows AWS KMS to use cryptographic keys that remain fully under customer control inside a Securosys Primus HSM or CloudHSM.
Keys are never imported into AWS, enabling strong key sovereignty, clear separation of duties, and compliance with strict regulatory or organizational requirements. This integration is designed for customers who want to use AWS KMS while retaining external ownership of their keys.
Learn more.webp?length=680&name=AWS%20logo%20(1).webp) AWS Bring Your Own Key (BYOK)
AWS Bring Your Own Key (BYOK)
AWS Bring Your Own Key (BYOK) with Securosys enables organizations to generate encryption keys in a Securosys Primus HSM or CloudHSM and import them into AWS KMS.
This approach provides stronger assurance over key origin and lifecycle compared to fully cloud-generated keys, while maintaining native integration with AWS services. It is well suited for compliance-driven environments that require customer-controlled key generation.
 Azure Bring Your Own Key (BYOK)
Azure Bring Your Own Key (BYOK)
Securosys CloudHSM or Primus HSM seamlessly integrate with Azure Key Vault, allowing encryption keys to be generated and managed in Primus HSM or CloudHSM and used within Azure Key Vault.
By keeping key creation and lifecycle control outside the cloud platform, organizations can meet regulatory, audit, and data sovereignty requirements more easily. The integration combines Azure’s encryption capabilities with customer-held, HSM-protected keys.
 CyberArk Privileged Access Manager (PAM)
CyberArk Privileged Access Manager (PAM)
Integrating Securosys Primus HSM with CyberArk’s Self-Hosted Privileged Access Manager, protects cryptographic keys used to secure privileged credentials and access workflows. Keys are generated and used inside certified hardware, strengthening trust in credential protection and reducing exposure to software-based attacks.
This integration supports regulated environments that require strong assurance for privileged access security. secures privileged accounts and SSH keys through true-RNG key generation and hardware-protected key storage, by ensuring compliance and full lifecycle key management in a highly scalable and secure manner.
 Cloudflare Keyless SSL
Cloudflare Keyless SSL
Cloudflare Keyless SSL when integrated with Securosys Primus HSM, enables organizations to use Cloudflare’s global edge network without ever exposing their private TLS keys. Private keys remain securely stored inside a tamper-resistant Securosys HSM, which performs all cryptographic signing operations during TLS handshakes.
This integration combines high-performance TLS termination with strong key sovereignty, compliance, and reduced risk of key compromise.
 Delinea Privileged Access Manager (PAM)
Delinea Privileged Access Manager (PAM)
Delinea Secret Server integrates with Securosys Primus HSM and CloudHSM to strengthen the protection of privileged credentials and encryption keys. Cryptographic keys are generated, stored, and used exclusively within certified hardware, reducing exposure to software-based attacks and supporting strict compliance requirements.
This integration enhances the security of privileged access management while supporting both on-premises and cloud deployments.
As containerization continues to rise in popularity, ensuring the security of containerized applications has become increasingly important.
Ensure the integrity of your containerized applications with Securosys Primus HSM. By leveraging Primus HSM’ sophisticated authorizations, such as quorums and time-restricted workflows enabled by Smart Key Attributes (SKA), Docker image signing is secure and compliant.
Learn moreAs containerization continues to rise in popularity, ensuring the security of containerized applications has become increasingly important.
With Securosys CloudHSM or Primus HSM, securely encrypt Docker images and ensure their confidentiality. Through integration with Securosys Transaction Security Broker (TSB) and REST APIs, Docker image encryption and signing become seamless processes.
Learn more Evertrust Stream
Evertrust Stream integrates with Securosys Primus HSM or CloudHSM to secure certificate authority operations with hardware-backed key protection. All critical CA keys are generated and used inside the HSM, ensuring that certificate issuance, signing, and lifecycle operations never expose private keys. This integration supports scalable, high-availability PKI deployments with strong security and compliance guarantees.
Learn more
Evertrust Stream
Evertrust Stream integrates with Securosys Primus HSM or CloudHSM to secure certificate authority operations with hardware-backed key protection. All critical CA keys are generated and used inside the HSM, ensuring that certificate issuance, signing, and lifecycle operations never expose private keys. This integration supports scalable, high-availability PKI deployments with strong security and compliance guarantees.
Learn more
 Fireblocks
Fireblocks
Fireblocks integrates with Securosys Primus HSM through Fireblocks Key Link, allowing organizations to secure blockchain wallet keys inside certified hardware. Instead of relying solely on MPC-based key splitting, this integration enables full ownership, tamper-resistant key storage, and reuse of existing HSM security processes.
It is particularly suited for regulated financial institutions requiring high assurance, performance, and compliance in digital asset custody.
Learn more F5 BIG-IP
F5 BIG-IP integrates with Securosys Primus HSM to securely store and use TLS private keys for SSL/TLS termination and offload. Cryptographic operations are performed by the HSM, ensuring private keys remain protected while maintaining high performance and availability. This integration supports compliance requirements for hardware-backed key protection in application delivery environments.
Learn more
F5 BIG-IP
F5 BIG-IP integrates with Securosys Primus HSM to securely store and use TLS private keys for SSL/TLS termination and offload. Cryptographic operations are performed by the HSM, ensuring private keys remain protected while maintaining high performance and availability. This integration supports compliance requirements for hardware-backed key protection in application delivery environments.
Learn more
HashiCorp Vault Community Edition implements a platform-agnostic, REST-based interface for HSMs, requiring no library installation. By leveraging secure TLS connections, it removes connectivity barriers, making deployment in clustered and multi-cloud environments straightforward.
Securosys Primus HSM offers added security innovations, such as hardware-enforced multi-authorization workflows, enhancing compliance and operational security from the start. Unlock your Vault with the seamless integration and protection of our HSMs, ensuring secure key management and cryptographic operations for your compliance applications.
Learn moreSecurosys Secret Engine is a plugin that integrates HSMs with Vault, allowing users to generate, manage, and protect secrets using the strong cryptographic capabilities of Securosys Primus HSM. This plugin features a platform-agnostic REST-based HSM interface with zero library installation, simplifying deployment in clustered and multi-cloud environments through secure TLS connections.
With Securosys Primus HSM, users can perform secure cryptographic operations and manage keys within the HSM, utilizing advanced features like high-performance encryption (ECIES, AES-GCM) and compliance-focused multi-authorization workflows, signature services, or blockchain transactions.
Learn moreKeyfactor EJBCA integrates with Securosys Primus HSM and CloudHSM to protect CA private keys with hardware-backed security across both Enterprise and Community editions.
The integration supports traditional PKCS#11 as well as the Securosys REST API, enabling modern, cloud-friendly deployments without the complexity of PKCS#11 where required. Using the Securosys REST API, EJBCA can also leverage NIST-selected post-quantum cryptographic (PQC) algorithms and advanced key governance features such as Smart Key Attributes (SKA), supporting future-ready and compliance-driven PKI environments.
Knot DNS integrates with Securosys Primus HSM via PKCS#11 to securely generate and store DNSSEC signing keys. By delegating key generation and signing operations to the HSM, DNSSEC keys remain protected throughout their lifecycle.
The integration supports high-performance, high-availability DNSSEC deployments with professional key management.
Learn more MariaDB
MariaDB
MariaDB integrates with Securosys Primus HSM and CloudHSM to protect encryption keys used for data-at-rest encryption. Encryption keys are secured inside the HSM, ensuring sensitive database content is only decrypted in memory and never stored in plaintext on disk.
This integration supports stronger protection of confidential data while aligning with compliance and audit requirements.
Learn more Microsoft Active Directory Certificate Services (AD CS)
Microsoft Active Directory Certificate Services (AD CS)
AD CS is a certificate authority (CA) that issues, manages, and validates the digital identities used to verify an individual or a system. The trust of the entire system and validity of each issued certificate depends upon the protection of the CA key issuing the identities.
By integrating with Securosys Primus HSM, secure your Microsoft PKI private keys for comprehensive protection and compliance. Integrate easily with Microsoft’s CNG API for secure key operations.
Learn more Microsoft Internet Information Services
Microsoft Internet Information Services
Secure the private keys used for Microsoft IIS by integrating with Securosys Primus HSM, available both on-premises and in the cloud. IIS, a versatile and secure web server for hosting applications, can interface with MS SharePoint, Visual Studio .NET, ASP.NET, and WebDAV.
With support from the MS Cryptography Next Generation (CNG) API, IIS can create and manage private keys and cryptographic functions directly on Primus HSM, meeting new compliance requirements like GDPR.
Learn more Microsoft SignTool
Microsoft SignTool
The Microsoft SignTool is a command-line CryptoAPI tool used for digitally signing, verifying, or timestamping files, codes, libraries, and documents. It is part of the Microsoft Windows Software Development Kit (SDK) and Visual Studio.
When combined with SignTool, Securosys Primus HSM enhances security practices by ensuring that all certificate issuance and validation processes occur within the protected environment of the HSM, keeping private keys inaccessible outside the HSM.
Learn more Microsoft SQL Always Encrypted
Protect sensitive data in transit and at rest by using Securosys Primus HSM to manage encryption keys in Microsoft SQL Server’s “Always Encrypted” feature. Ensure regulatory compliance and robust data security.
Learn more
Microsoft SQL Always Encrypted
Protect sensitive data in transit and at rest by using Securosys Primus HSM to manage encryption keys in Microsoft SQL Server’s “Always Encrypted” feature. Ensure regulatory compliance and robust data security.
Learn more
 Microsoft S/MIME
Microsoft S/MIME integrates with Securosys Primus HSM and CloudHSM to secure private keys used for email signing and encryption. By storing S/MIME keys in certified hardware, organizations significantly reduce the risk of key duplication or misuse.
Learn more
Microsoft S/MIME
Microsoft S/MIME integrates with Securosys Primus HSM and CloudHSM to secure private keys used for email signing and encryption. By storing S/MIME keys in certified hardware, organizations significantly reduce the risk of key duplication or misuse.
Learn more
 Microsoft Host Guardian Service
Microsoft Host Guardian Service
Microsoft Host Guardian Service integrates with Securosys Primus HSM to protect the keys used for shielded virtual machines. The HSM securely stores and controls access to encryption and signing keys, ensuring they are only released to trusted, verified hosts.
This integration enhances trust, integrity, and compliance for protected virtualized environments.
Learn more OpenBao
OpenBao is an identity-based secrets and encryption management system, forked from HashiCorp Vault. By integrating with Securosys HSMs, it supports auto-unsealing, removing the need for manual operator intervention and enhancing availability.
Learn more
OpenBao
OpenBao is an identity-based secrets and encryption management system, forked from HashiCorp Vault. By integrating with Securosys HSMs, it supports auto-unsealing, removing the need for manual operator intervention and enhancing availability.
Learn more
 Oracle
Oracle Transparent Database Encryption (TDE) integrates with Securosys Primus HSM and CloudHSM to protect database encryption keys. Keys are generated and used within the secure boundary of the HSM, preventing unauthorized access at the operating system level.
Learn more
Oracle
Oracle Transparent Database Encryption (TDE) integrates with Securosys Primus HSM and CloudHSM to protect database encryption keys. Keys are generated and used within the secure boundary of the HSM, preventing unauthorized access at the operating system level.
Learn more
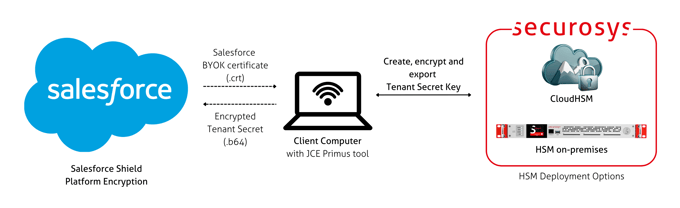
 Salesforce Bring Your Own Key (BYOK)
Integrate Securosys CloudHSM or Primus HSM on-premises with Salesforce Shield Platform Encryption to manage your encryption keys independently and maintain control over your data. This integration supports key rotation and compliance with stringent data protection standards.
Learn more
Salesforce Bring Your Own Key (BYOK)
Integrate Securosys CloudHSM or Primus HSM on-premises with Salesforce Shield Platform Encryption to manage your encryption keys independently and maintain control over your data. This integration supports key rotation and compliance with stringent data protection standards.
Learn more
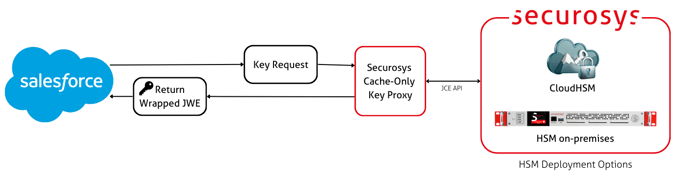
 Salesforce Cache-Only Key Service
Salesforce Cache-Only Key Service
Salesforce Cache-Only Key Service integrates with Securosys Primus HSM and CloudHSM to give customers strong control over encryption keys without sacrificing performance. Keys are securely generated and managed in the HSM and only cached temporarily within Salesforce, allowing rapid revocation while avoiding constant external key lookups.
This integration balances key ownership, operational resilience, and high-performance encryption for sensitive Salesforce data.
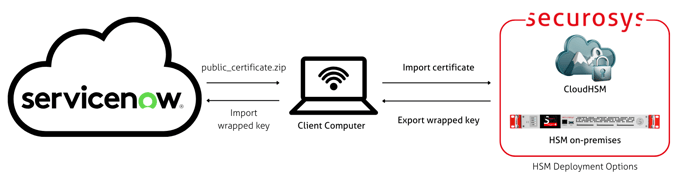
 ServiceNow Bring Your Own Key (BYOK)
ServiceNow Bring Your Own Key (BYOK)
ServiceNow BYOK integrates with Securosys Primus HSM and CloudHSM to allow customer-generated encryption keys to be used within the ServiceNow platform. Keys are created and wrapped inside the HSM, giving organizations control over key origin and lifecycle while using ServiceNow’s native encryption features.
This integration is suited for customers who require customer-managed keys for compliance and governance reasons.
 Sixscape IDcentral Key Management
Leverage Securosys Primus HSM for secure S/MIME key escrow with Sixscape’s IDcentral Key Management Platform. Ensure centralized, compliant storage of cryptographic keys, enabling secure data recovery and continuity.
Learn more
Sixscape IDcentral Key Management
Leverage Securosys Primus HSM for secure S/MIME key escrow with Sixscape’s IDcentral Key Management Platform. Ensure centralized, compliant storage of cryptographic keys, enabling secure data recovery and continuity.
Learn more
Venafi integrates with Securosys Primus HSM and CloudHSM to secure cryptographic keys used for managing machine identities at scale. Private keys for certificates and identities remain protected inside certified hardware, supporting compliance and reducing operational risk across large infrastructures.
The integration is designed for enterprises managing high volumes of machine identities with strong security and lifecycle control requirements.
 Versasec Credential Management System
Combine the capabilities of Versasec’s vSEC with Securosys Primus HSM for secure PKI administration. Enjoy options for on-premises or cloud-based HSMs and seamless key management.
Learn more
Versasec Credential Management System
Combine the capabilities of Versasec’s vSEC with Securosys Primus HSM for secure PKI administration. Enjoy options for on-premises or cloud-based HSMs and seamless key management.
Learn more
 White Rabbit's OpenXPKI Enterprise
Deploy White Rabbit’s OpenXPKI Enterprise integrated with Securosys Primus HSM for centralized digital certificate management. This integration supports configuration automation and compliance audits for enhanced security.
Learn more
White Rabbit's OpenXPKI Enterprise
Deploy White Rabbit’s OpenXPKI Enterprise integrated with Securosys Primus HSM for centralized digital certificate management. This integration supports configuration automation and compliance audits for enhanced security.
Learn more
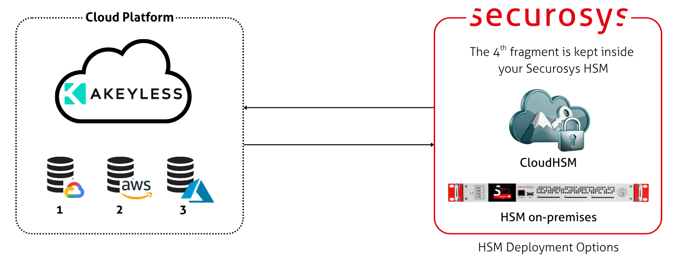
Akeyless Secrets Management Platform
The Akeyless Gateway integration allows organizations to combine Akeyless’ Distributed Fragments Cryptography (DFC) with Securosys Primus HSM or CloudHSM for customer-controlled key fragments.
By storing the customer fragment securely inside a certified HSM, organizations retain direct control over a critical part of the encryption key while benefiting from Akeyless’ distributed secrets management architecture. This setup strengthens key ownership, reduces exposure risk, and supports highly secure, multi-cloud secrets protection.
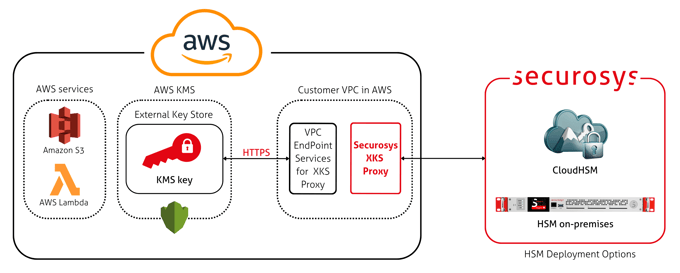
Securosys Proxy for AWS External Key Store (XKS)
The Securosys Proxy for AWS External Key Store (XKS) allows AWS KMS to use cryptographic keys that remain fully under customer control inside a Securosys Primus HSM or CloudHSM.
Keys are never imported into AWS, enabling strong key sovereignty, clear separation of duties, and compliance with strict regulatory or organizational requirements. This integration is designed for customers who want to use AWS KMS while retaining external ownership of their keys.
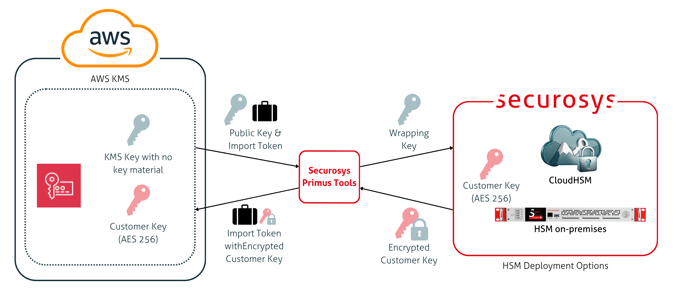
AWS Bring Your Own Key (BYOK)
AWS Bring Your Own Key (BYOK) with Securosys enables organizations to generate encryption keys in a Securosys Primus HSM or CloudHSM and import them into AWS KMS.
This approach provides stronger assurance over key origin and lifecycle compared to fully cloud-generated keys, while maintaining native integration with AWS services. It is well suited for compliance-driven environments that require customer-controlled key generation.
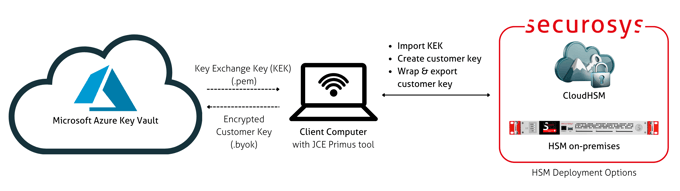
Azure Bring Your Own Key (BYOK)
Securosys CloudHSM or Primus HSM seamlessly integrate with Azure Key Vault, allowing encryption keys to be generated and managed in Primus HSM or CloudHSM and used within Azure Key Vault.
By keeping key creation and lifecycle control outside the cloud platform, organizations can meet regulatory, audit, and data sovereignty requirements more easily. The integration combines Azure’s encryption capabilities with customer-held, HSM-protected keys.
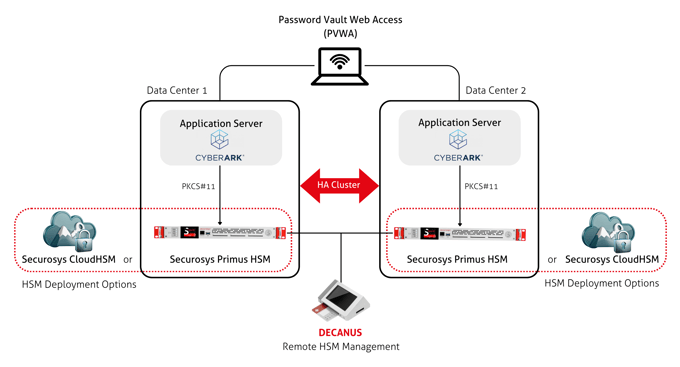
CyberArk Privileged Access Manager (PAM)
Integrating Securosys Primus HSM with CyberArk’s Self-Hosted Privileged Access Manager, protects cryptographic keys used to secure privileged credentials and access workflows. Keys are generated and used inside certified hardware, strengthening trust in credential protection and reducing exposure to software-based attacks.
This integration supports regulated environments that require strong assurance for privileged access security. secures privileged accounts and SSH keys through true-RNG key generation and hardware-protected key storage, by ensuring compliance and full lifecycle key management in a highly scalable and secure manner.
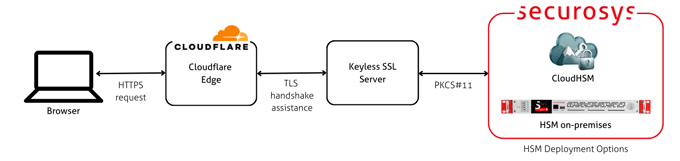
Cloudflare Keyless SSL
Cloudflare Keyless SSL when integrated with Securosys Primus HSM, enables organizations to use Cloudflare’s global edge network without ever exposing their private TLS keys. Private keys remain securely stored inside a tamper-resistant Securosys HSM, which performs all cryptographic signing operations during TLS handshakes.
This integration combines high-performance TLS termination with strong key sovereignty, compliance, and reduced risk of key compromise.
Delinea Privileged Access Manager (PAM)
Delinea Secret Server integrates with Securosys Primus HSM and CloudHSM to strengthen the protection of privileged credentials and encryption keys. Cryptographic keys are generated, stored, and used exclusively within certified hardware, reducing exposure to software-based attacks and supporting strict compliance requirements.
This integration enhances the security of privileged access management while supporting both on-premises and cloud deployments.
Docker Image Signing
As containerization continues to rise in popularity, ensuring the security of containerized applications has become increasingly important.
Ensure the integrity of your containerized applications with Securosys Primus HSM. By leveraging Primus HSM’ sophisticated authorizations, such as quorums and time-restricted workflows enabled by Smart Key Attributes (SKA), Docker image signing is secure and compliant.
Docker Image Encryption
As containerization continues to rise in popularity, ensuring the security of containerized applications has become increasingly important.
With Securosys CloudHSM or Primus HSM, securely encrypt Docker images and ensure their confidentiality. Through integration with Securosys Transaction Security Broker (TSB) and REST APIs, Docker image encryption and signing become seamless processes.
Evertrust Stream
Fireblocks
Fireblocks integrates with Securosys Primus HSM through Fireblocks Key Link, allowing organizations to secure blockchain wallet keys inside certified hardware. Instead of relying solely on MPC-based key splitting, this integration enables full ownership, tamper-resistant key storage, and reuse of existing HSM security processes.
It is particularly suited for regulated financial institutions requiring high assurance, performance, and compliance in digital asset custody.
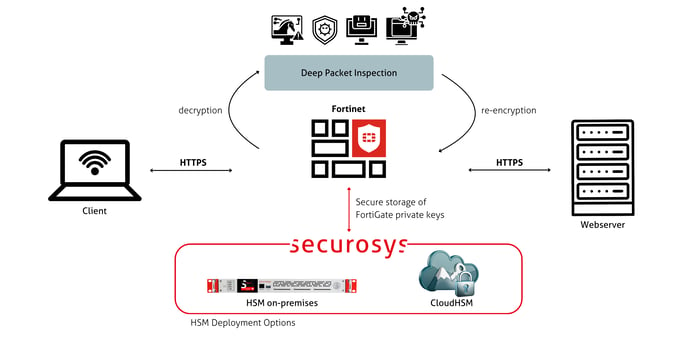
Fortinet
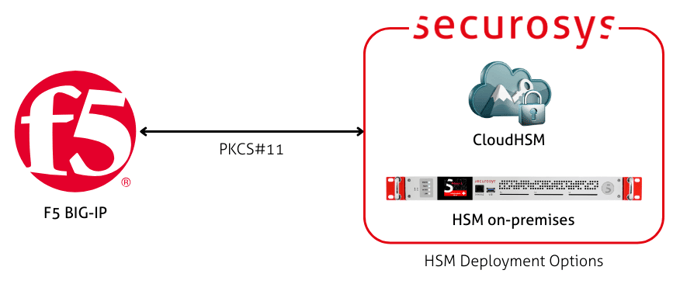
F5 BIG-IP
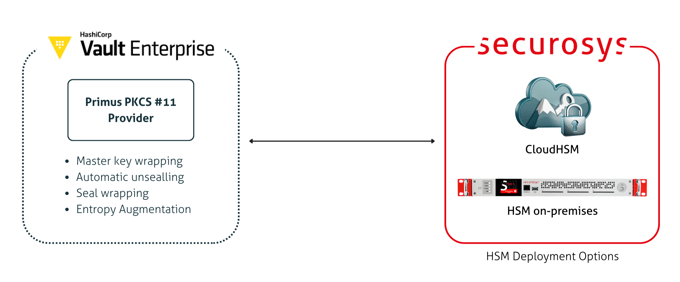
HashiCorp Vault Enterprise
HashiCorp Vault Community
HashiCorp Vault Community Edition implements a platform-agnostic, REST-based interface for HSMs, requiring no library installation. By leveraging secure TLS connections, it removes connectivity barriers, making deployment in clustered and multi-cloud environments straightforward.
Securosys Primus HSM offers added security innovations, such as hardware-enforced multi-authorization workflows, enhancing compliance and operational security from the start. Unlock your Vault with the seamless integration and protection of our HSMs, ensuring secure key management and cryptographic operations for your compliance applications.
HashiCorp Vault Secret Engine
Securosys Secret Engine is a plugin that integrates HSMs with Vault, allowing users to generate, manage, and protect secrets using the strong cryptographic capabilities of Securosys Primus HSM. This plugin features a platform-agnostic REST-based HSM interface with zero library installation, simplifying deployment in clustered and multi-cloud environments through secure TLS connections.
With Securosys Primus HSM, users can perform secure cryptographic operations and manage keys within the HSM, utilizing advanced features like high-performance encryption (ECIES, AES-GCM) and compliance-focused multi-authorization workflows, signature services, or blockchain transactions.
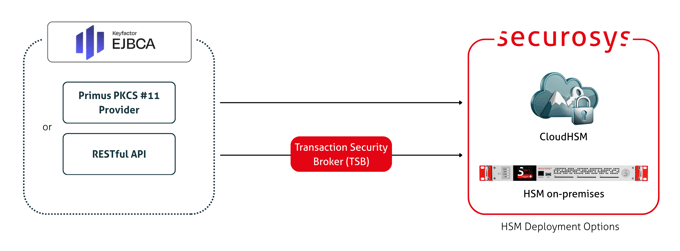
Keyfactor EJBCA
Keyfactor EJBCA integrates with Securosys Primus HSM and CloudHSM to protect CA private keys with hardware-backed security across both Enterprise and Community editions.
The integration supports traditional PKCS#11 as well as the Securosys REST API, enabling modern, cloud-friendly deployments without the complexity of PKCS#11 where required. Using the Securosys REST API, EJBCA can also leverage NIST-selected post-quantum cryptographic (PQC) algorithms and advanced key governance features such as Smart Key Attributes (SKA), supporting future-ready and compliance-driven PKI environments.
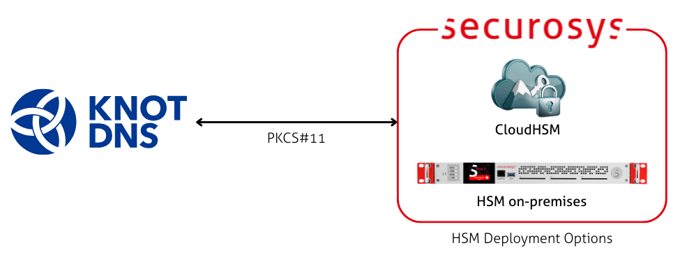
Knot DNS
Knot DNS integrates with Securosys Primus HSM via PKCS#11 to securely generate and store DNSSEC signing keys. By delegating key generation and signing operations to the HSM, DNSSEC keys remain protected throughout their lifecycle.
The integration supports high-performance, high-availability DNSSEC deployments with professional key management.
MariaDB
MariaDB integrates with Securosys Primus HSM and CloudHSM to protect encryption keys used for data-at-rest encryption. Encryption keys are secured inside the HSM, ensuring sensitive database content is only decrypted in memory and never stored in plaintext on disk.
This integration supports stronger protection of confidential data while aligning with compliance and audit requirements.
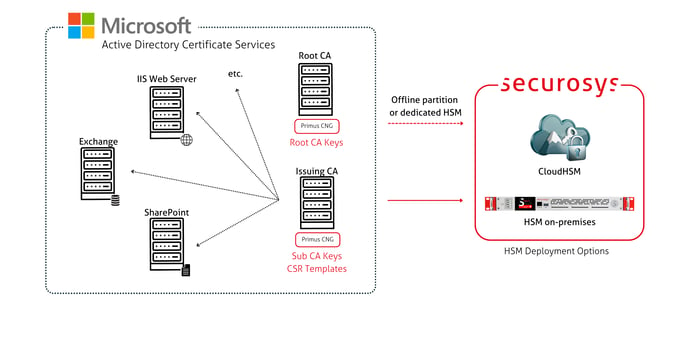
Microsoft Active Directory Certificate Services (AD CS)
AD CS is a certificate authority (CA) that issues, manages, and validates the digital identities used to verify an individual or a system. The trust of the entire system and validity of each issued certificate depends upon the protection of the CA key issuing the identities.
By integrating with Securosys Primus HSM, secure your Microsoft PKI private keys for comprehensive protection and compliance. Integrate easily with Microsoft’s CNG API for secure key operations.
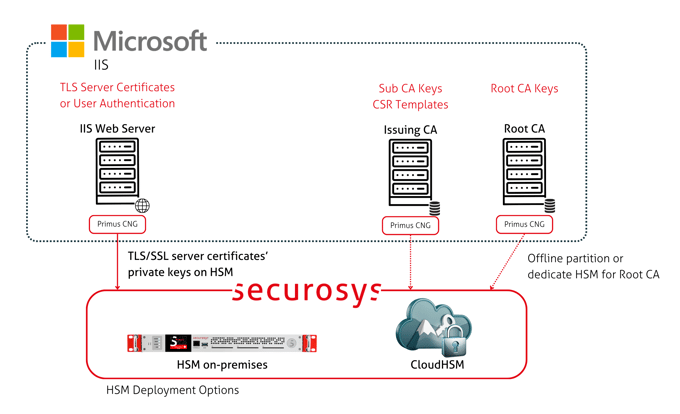
Microsoft Internet Information Services
Secure the private keys used for Microsoft IIS by integrating with Securosys Primus HSM, available both on-premises and in the cloud. IIS, a versatile and secure web server for hosting applications, can interface with MS SharePoint, Visual Studio .NET, ASP.NET, and WebDAV.
With support from the MS Cryptography Next Generation (CNG) API, IIS can create and manage private keys and cryptographic functions directly on Primus HSM, meeting new compliance requirements like GDPR.
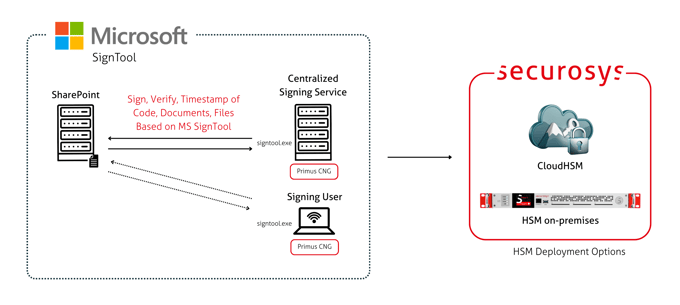
Microsoft SignTool
The Microsoft SignTool is a command-line CryptoAPI tool used for digitally signing, verifying, or timestamping files, codes, libraries, and documents. It is part of the Microsoft Windows Software Development Kit (SDK) and Visual Studio.
When combined with SignTool, Securosys Primus HSM enhances security practices by ensuring that all certificate issuance and validation processes occur within the protected environment of the HSM, keeping private keys inaccessible outside the HSM.
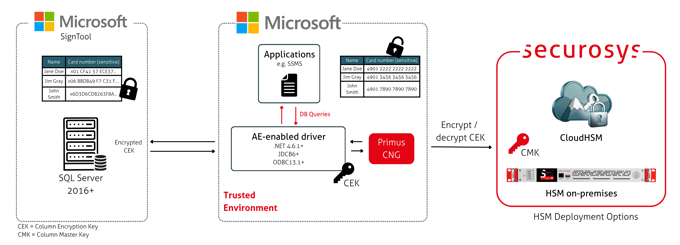
Microsoft SQL Always Encrypted
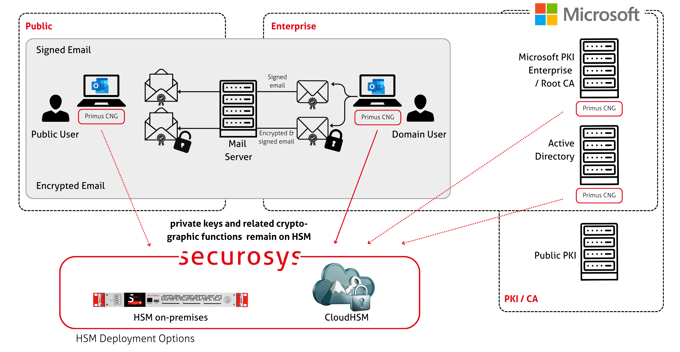
Microsoft S/MIME
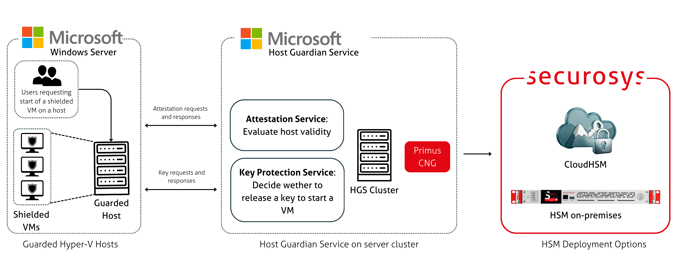
Microsoft Host Guardian Service
Microsoft Host Guardian Service integrates with Securosys Primus HSM to protect the keys used for shielded virtual machines. The HSM securely stores and controls access to encryption and signing keys, ensuring they are only released to trusted, verified hosts.
This integration enhances trust, integrity, and compliance for protected virtualized environments.
MTG Enterprise Resource Security
OpenBao
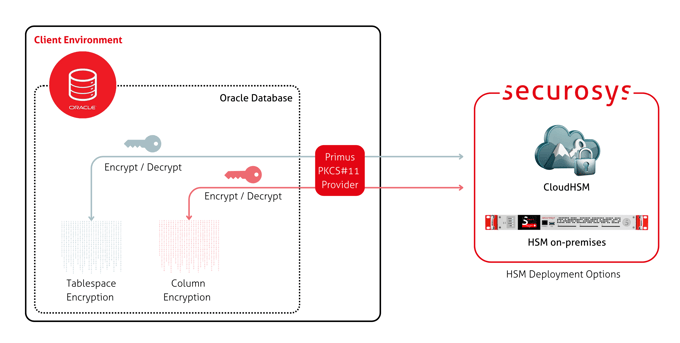
Oracle
Salesforce Bring Your Own Key (BYOK)
Salesforce Cache-Only Key Service
Salesforce Cache-Only Key Service integrates with Securosys Primus HSM and CloudHSM to give customers strong control over encryption keys without sacrificing performance. Keys are securely generated and managed in the HSM and only cached temporarily within Salesforce, allowing rapid revocation while avoiding constant external key lookups.
This integration balances key ownership, operational resilience, and high-performance encryption for sensitive Salesforce data.
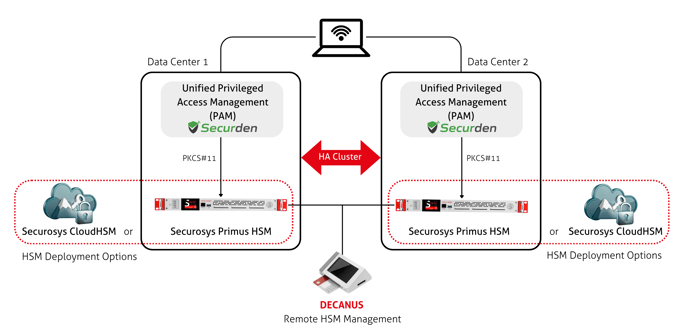
Securden Unified PAM
ServiceNow Bring Your Own Key (BYOK)
ServiceNow BYOK integrates with Securosys Primus HSM and CloudHSM to allow customer-generated encryption keys to be used within the ServiceNow platform. Keys are created and wrapped inside the HSM, giving organizations control over key origin and lifecycle while using ServiceNow’s native encryption features.
This integration is suited for customers who require customer-managed keys for compliance and governance reasons.

Sixscape IDcentral Key Management
Venafi Machine Identity Management
Venafi integrates with Securosys Primus HSM and CloudHSM to secure cryptographic keys used for managing machine identities at scale. Private keys for certificates and identities remain protected inside certified hardware, supporting compliance and reducing operational risk across large infrastructures.
The integration is designed for enterprises managing high volumes of machine identities with strong security and lifecycle control requirements.