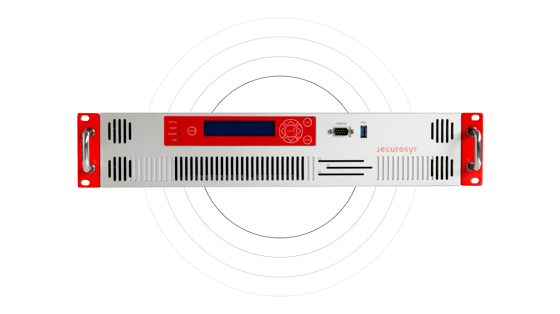
Primus Blockchain HSM
Challenge
Frequent news headlines highlight the loss or theft of crypto assets worth millions of dollars. However, this issue is not inherent to blockchain or distributed ledger technology. In these instances of theft, the private keys were inadequately stored, left minimally protected in server filesystems. If you are involved in managing crypto keys, particularly those entrusted to you by customers or involved in custody services, it's crucial to consider securing the private keys using hardware security modules

Solution
Effortlessly secure blockchain systems and crypto assets with the Securosys Primus Blockchain HSM. We offer enterprise-grade security, continually enhanced with additional functionalities to safeguard new blockchain systems entering the market.
Built upon the Primus X-Series and E-Series HSM, Primus Blockchain HSM introduces exclusive features to Distributed Ledger Technology (DLT), enabling applications to prioritize business functionality while entrusting blockchain security and key access management to the Blockchain HSM.

Key Benefits
.webp?length=120&name=image%20(4).webp)
-2.webp?length=120&name=image%20(2)-2.webp)
.webp?length=120&name=image%20(5).webp)


Market-Leading Performance
The Blockchain HSM supports performance needs from small transactions to up to 50,000 concurrent transactions per second, scalable to over 1,000,000 in clustered environments, solidifying its pioneering role.
Segregated Functions
Maintain strict separation between business logic and security within the Blockchain HSM, even in virtual or cloud setups. Securosys Smart Key Attributes (SKA) ensure regulatory compliance by securely segregating client and exchange assets, eliminating omnibus accounts and asset co-mingling.
Large Storage Space
Benefit from up to 30 GB of storage, enabling secure management of both cold and hot wallet keys on a single HSM.
Success Stories
Revolutionizing Secure Blockchain Asset Management with Crypto Storage AG
Crypto Storage AG, in collaboration with Securosys, has redefined secure blockchain asset management for financial intermediaries. This partnership not only led to groundbreaking innovations, including two patent applications but also set new industry benchmarks, ensuring secure, tamper-proof transactions without compromising usability.
Discover how Crypto Storage AG is leading the way in crypto asset security.
KORE Technologies and Securosys: Building a Secure, End-to-End Digital Asset Management Platform
KORE Technologies developed a comprehensive digital asset management platform that ensures top-tier security, availability, and regulatory compliance throughout the entire asset life cycle. By partnering with Securosys, KORE leveraged the advanced capabilities of the Primus hardware security modules (HSM), addressing critical challenges such as fraud prevention and quantum resilience. This collaboration allowed KORE to focus on seamless integration and user experience, creating a robust platform that meets the stringent demands of modern financial institutions.
Discover how KORE Technologies, with Securosys, is revolutionizing digital asset management.
Technical Specifications
- The HSM has a dual True Random Generator TRNG entropy source, and NIST SP800-90 compliant RNG
- Key derivation on asymmetric keys including built-in BIP 32
- Direct secure address generation (hash of the public key), which delivers extra PQC protection in the HSM
- Prevents extraction of keys without compromising the storage
- Cannot be compromised by software bugs
- Prevents attack by silicon vendor
- Mitigates risk from compromised software interacting with business logic
- Process segregation that reduces risks associated with the communication stack being compromised
- Side channel protection
- Protection from Spectre / Meltdown kind of attacks
- Field upgradable FPGA implementation
- Segregation of duties avoids risks with single admin having all information
- Mitigates risks associated with hacked admin accounts
- Device clustering for HA redundancy and performance scalablity with integrated secure backup feature
- Integrated multi-signature authentication scheme
- ETH, BTC based, Ripple, IOTA and many more, ... and many more, including derivatives of top crypto currencies













Related Products
 Primus HSM X-Series
Ideal hardware for advanced encryption standards and digital signatures
Primus HSM X-Series
Ideal hardware for advanced encryption standards and digital signatures
 Smart Key Attributes
Fortifying your encryption keys security with Smart Key Attributes
Smart Key Attributes
Fortifying your encryption keys security with Smart Key Attributes
 Transaction Security Broker
Unique transaction security for financial and digital assets applications
Transaction Security Broker
Unique transaction security for financial and digital assets applications
 Decanus Terminal
Remotely manage your HSM and user partitions
Decanus Terminal
Remotely manage your HSM and user partitions











