Achieving Data Sovereignty on AWS: The Role of External Key Stores

Amazon Web Services (AWS) is a leading provider of public cloud services, offering diverse solutions to individuals and enterprises globally. However, as data processing and storage in the public cloud increase, concerns about data privacy become paramount. In response, AWS offers the AWS Key Management Service (KMS) for data encryption. Nevertheless, when compliance mandates dictate that encryption keys for regulated workloads must reside outside AWS and remain solely under your control, External Key Stores (XKS) offer a robust solution. This blog post introduces the concept of XKS and highlights the benefits of using Securosys AWS XKS proxy.
Enhancing Control with External Key Stores
While AWS KMS provides encryption capabilities, a significant drawback is the lack of control over key resource policies. With keys maintained and controlled by AWS, users may face challenges in restricting access, potentially leading to sovereignty and compliance issues. External Key Stores enhance the KMS key hierarchy with an external root of trust, offering complete control over cryptographic keys and data.
How Do External Key Stores Work?
External Key Stores enable the protection of AWS resources using cryptographic keys outside AWS infrastructure. XKS operates as a custom key store backed by an external key manager, such as a physical or virtual hardware security module (HSM). AWS KMS interacts only with an external key store proxy (XKS proxy) software provided by users, ensuring no direct access to the keys. The keys are managed on AWS KMS but created, used, and stored on an HSM.
Benefits of Securosys External Key Stores
Digital Sovereignty: Gain complete control over data within AWS, eliminating the need to rely solely on AWS KMS, by hosting your own keys.
Compliance: The Securosys XKS solution – built on Securosys Primus HSM - complies with certifications like FIPS 140-2/3 L3 and CC EAL 4+, adhering to the highest industry standards.
Enhanced Security: Your cryptographic keys reside outside of the AWS KMS cloud, ensuring that only you can decrypt protected content and thus mitigating the risk of unauthorized access.
Scalability: Securosys Primus HSM clustering offers support for multi-region setups. The Proxy has the flexibility to be deployed either on-premises or in the cloud and can seamlessly connect to both on-premises and CloudHSM environments.
Quick Deployment: Securosys AWS XKS Proxy can be swiftly deployed via a Docker Image, minimizing setup complexities.
Cost Efficiency: No additional costs or overhead occur for additional KMS services as you are directly linked to the HSM.
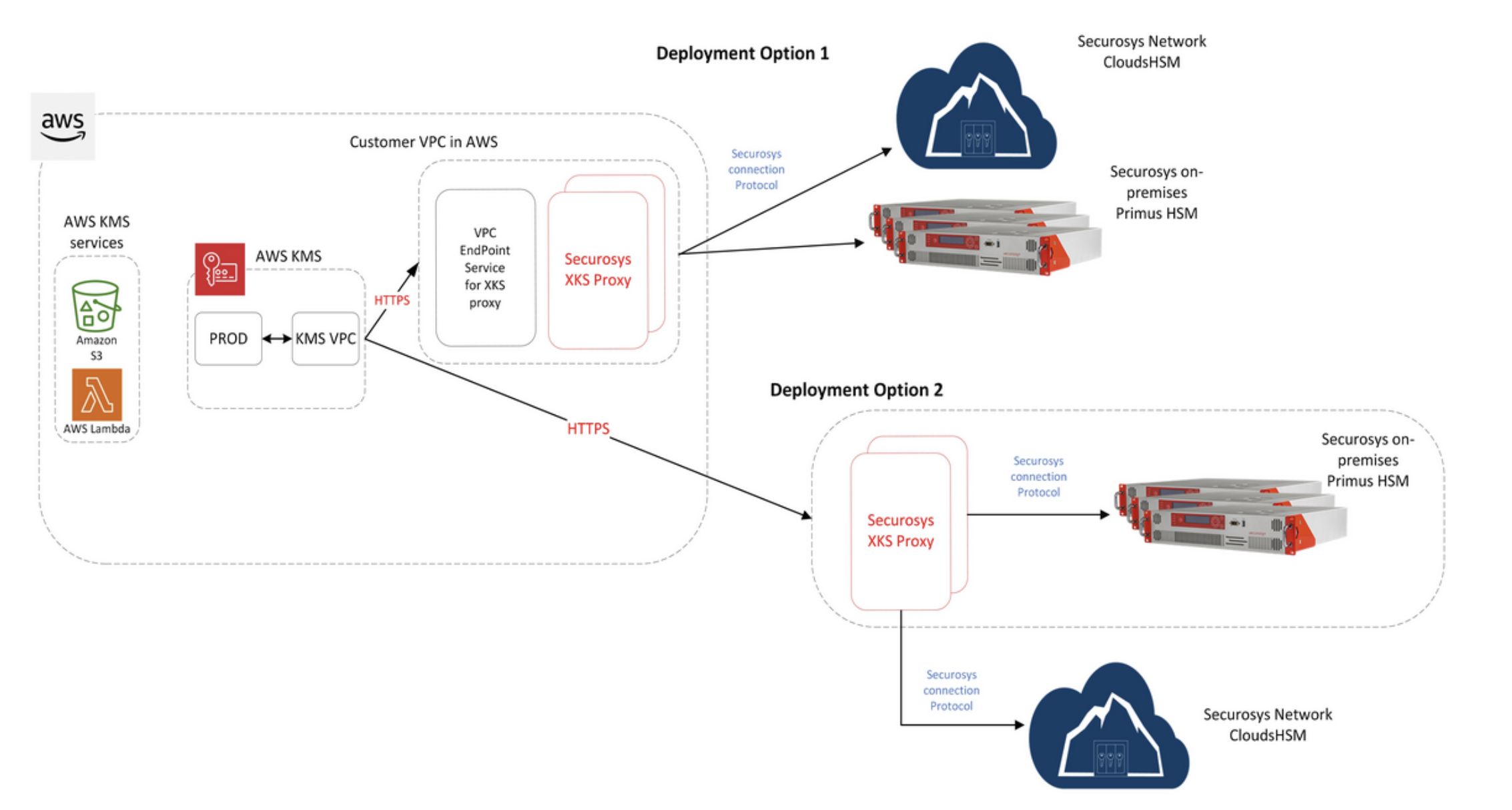
How Does Securosys XKS Proxy Works with AWS Services?
The Securosys XKS Proxy acts as a secure intermediary between AWS KMS and your Securosys Primus HSM or CloudHSM, ensuring no direct engagement with your HSM.
Our custom XKS proxy, packaged as a Docker image, is maintained by our in-house specialists and available for customer deployment whenever needed. Deployment is simple and adaptable, whether within an AWS EC2 instance or in your own environment.
For a step-by-step instruction on how to deploy Securosys AWS XKS Proxy, please download our application note.
As businesses entrust their data to AWS, ensuring data sovereignty is imperative. Adopting External Key Stores, such as Securosys AWS XKS Proxy, coupled with Securosys on-premises HSM or CloudHSM, offers a quick and user-friendly strategy to maintain sovereignty over data. By assuming control of cryptographic keys, businesses preserve digital sovereignty and ensure compliance with industry regulations.